The Ultimate Guide to Web3 Wallet Security: Protecting Your Crypto Assets from Hackers

Rising Tide of Hacking Incidents
The crypto world has seen a surge in high-profile hacks. Bybit suffered a staggering $1.5 billion loss in digital assets, marking one of the largest crypto thefts in history. Hackers exploited multi-signature wallets by infecting each signer’s device with malware, causing the user interface to display fraudulent transaction details. This tricked all signers into approving changes to the ETH cold wallet’s smart contract logic without suspicion.
Just two days later, Infini reported a $50 million theft due to a compromised private key. These incidents highlight the growing sophistication and frequency of attacks. A single misstep can lead to the permanent loss of your assets.
In the Web3 and crypto ecosystem, wallets are your gateway to decentralized finance (DeFi), NFTs, on-chain gaming, and more. To help you safeguard your assets, Drhash presents this ultimate Web3 wallet security guide. Read it carefully and share it with friends! 👇
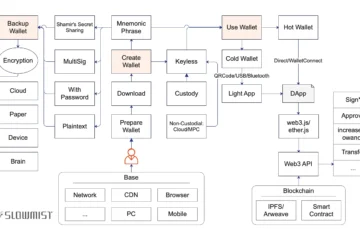
Wallet Security Guide
🔐 1. Private Keys and Seed Phrases: Your Lifeline
Your private key and seed phrase are the core of your wallet. Anyone who gains access to them has full control over your funds. Never share screenshots of your private key or seed phrase or store them in the cloud (e.g., WeChat favorites, Google Drive). Instead, write them down by hand and store them securely, such as in a safe.
Never enter your seed phrase on unknown websites or apps, even if they appear legitimate.
🛡️ 2. Use a Hardware Wallet
Hardware wallets are the safest storage option, as the private key never leaves the device. Store large amounts in a hardware wallet and use a hot wallet for small, daily transactions.
Always purchase hardware wallets through official channels to avoid tampered devices.
🎣 3. Beware of Phishing Attacks
Phishing websites, disguised as legitimate DApps or wallet interfaces, are a common tactic used by hackers. Always double-check the URL to confirm it’s the official domain, and avoid clicking suspicious links.
Be cautious of airdrop or reward links shared by unverified users on social media—many are phishing traps.
Install anti-phishing browser extensions to detect malicious websites.
🔍 4. Regularly Review Wallet Authorizations
When interacting with DApps, your wallet may grant smart contracts access to your assets. These authorizations can be exploited if malicious. Use tools to periodically check and revoke unnecessary permissions.
Only grant the minimum required permissions and avoid giving DApps unlimited access.
🔒 5. Enable Two-Factor Authentication (2FA)
For centralized exchanges or wallet services, always enable 2FA using tools like Google Authenticator or Authy, rather than SMS (which can be intercepted).
Back up your 2FA recovery codes in case you lose your device.
🎭 6. Guard Against Social Engineering
Hackers may pose as customer support, project teams, or influencers, contacting you via DMs, emails, or Telegram. Verify their identity multiple times to avoid scams.
Official teams will never initiate private messages or ask for your private key or seed phrase.
Always verify information through official channels (e.g., project websites or verified Twitter accounts).
💻 7. Secure Your Device
Install antivirus software and regularly scan your device to prevent malware from stealing wallet information. Avoid using public Wi-Fi for wallet access or transactions.
Keep your operating system and browser updated to patch known vulnerabilities.
🧩 8. Diversify Asset Risk
Don’t store all your assets in a single wallet. Spread them across multiple wallets, such as hardware and hot wallets, to reduce risk.
For long-term holdings, consider multi-signature wallets for added security.
🚨 9. What to Do If Your Assets Are Stolen
If you detect a theft, immediately transfer remaining assets to a secure wallet. Abandon the compromised wallet—don’t take chances.
Track stolen funds using tools like DeBank and report the theft to relevant platforms (e.g., exchanges or blockchain explorers) to attempt asset freezes.
🌐 10. Stay Informed and Vigilant
The Web3 landscape evolves rapidly, and so do hacking techniques. Stay updated on the latest security trends.
Join trusted communities (e.g., Discord, Telegram) to share and learn security best practices.
Conclusion
The Web3 world is full of opportunities but also fraught with risks. By securing your wallet, you can confidently navigate this decentralized future. Protect your assets, stay vigilant, and thrive in the crypto ecosystem.