Are Hardware Wallets 100% Safe? Two Types of Scams You Need to Know

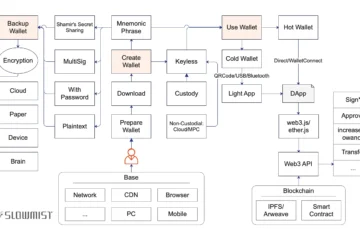
Hardware wallets are physical devices designed to securely store cryptocurrency, widely regarded as a robust solution for safeguarding digital assets. Equipped with secure chips, they store private keys offline, ensuring users retain full control over their crypto. By operating in an offline environment, hardware wallets significantly reduce the risk of internet-based hacking attempts.
However, many novice investors, unaware of potential vulnerabilities, fall victim to scams that result in the loss of assets stored in hardware wallets. This article highlights two prevalent scams targeting hardware wallet users: instruction manual fraud and tampered device scams.
Instruction Manual Fraud
This scam exploits users’ lack of familiarity with hardware wallet operations by substituting fake instruction manuals that trick victims into transferring funds to phishing addresses. A user purchases a hardware wallet from a third-party e-commerce platform, opens the package, and follows the “manual’s” instructions. These may include using a pre-set “initial PIN code” to unlock the device and backing up a “seed phrase” printed in the manual. After depositing funds into the wallet’s address, the assets are stolen.
The theft doesn’t stem from a hardware breach but from a sophisticated ruse. Scammers pre-activate the wallet, obtain its seed phrase, and repackage the device with a fraudulent manual. These tampered wallets are then sold through unofficial channels. Once the victim transfers crypto to the address, the funds are siphoned off in a standard fake wallet scam.
In Chinese-speaking markets, similar risks have emerged. The well-known hardware wallet manufacturer imKey issued a warning about non-official retailers selling “pre-activated” wallets with altered manuals, luring users into depositing funds into addresses controlled by malicious actors. This underscores the importance of purchasing from verified retailers, just as one would verify a legitimate website.
Tampered Device Scams
In another case, a Ledger user received an unsolicited package containing a brand-new Ledger X hardware wallet and a letter. The letter claimed that, due to a data breach at Ledger, the company was sending replacement wallets to affected customers and urged the user to switch devices for security.
However, Ledger’s CEO, Pascal Gauthier, clarified that the company would not compensate for data leaks in this manner. The user identified the package as a scam, sharing images revealing clear signs of tampering inside the wallet’s plastic casing.
Similarly, Kaspersky’s security team reported a case involving a counterfeit Trezor Model T purchased from an unofficial source. The device’s firmware had been modified by attackers, granting them access to the user’s crypto assets and enabling theft.
Key Takeaways
These cases illustrate the prevalence of supply chain attacks targeting hardware wallets. Both investors and manufacturers must remain vigilant. Adopting proper usage practices can significantly mitigate theft risks:
- Purchase from Official Channels: Hardware wallets bought from unofficial sources are inherently risky and should be avoided.
- Verify the Device Is Unactivated: Legitimate hardware wallets are sold unactivated. If a device appears pre-activated upon receipt, or if the manual references an “initial password” or “default address,” stop using it immediately and contact the manufacturer.
- Generate Addresses Yourself: Beyond activation, setting the PIN code, generating the seed phrase, and creating addresses must be done personally. Any third-party involvement in these steps introduces significant risks. Under normal circumstances, a hardware wallet should arrive unactivated, requiring the user to activate it, create a wallet, back up the seed phrase, and set a PIN code independently.
By following these precautions, users can protect their assets and navigate the Web3 ecosystem with greater confidence.