Key Security Concerns for Crypto Users

Security will likely remain a central topic in the crypto industry for at least the next decade, as it presents challenges in both decentralized and centralized ecosystems. Prompted by recent exchange security incidents, this article explores four critical areas crypto users must prioritize to protect their assets.
1. Asset Sovereignty
Decentralization grants users far greater control over their assets compared to centralized systems, a narrative that fueled the DeFi Summer and sparked the “withdraw to self-custody” movement. However, full asset sovereignty doesn’t always equate to enhanced security. As smart contract hacks and authorization-based thefts rise, managing assets on-chain demands significant expertise and risk awareness, creating a steep learning curve for many users.
Consequently, newer investors often opt to entrust their assets to exchanges or institutions, trading simplicity for reduced control. Today, exchanges and on-chain solutions cater to distinct user groups, each with unique risks. On-chain self-custody offers complete ownership but requires robust risk management skills. Centralized custody is user-friendly but exposes users to platform-related risks. There’s no perfect solution—understanding and respecting these trade-offs is key.
2. Smart Contract Security
“Risk always lies in the unknown.”
For DeFi projects, immutable, permissionless smart contracts are hailed as decentralized and tamper-proof. However, they aren’t inherently secure. Unforeseen code vulnerabilities can lead to catastrophic exploits, especially in immutable contracts where centralized intervention is impossible. Early DeFi projects saw numerous such failures.
Looking ahead, smart contract security will evolve through time and market testing. Simple contracts will “solidify” first, becoming fully decentralized and immutable, while more complex ones may incorporate emergency mechanisms to mitigate losses during critical failures (balanced by permission controls to avoid excessive centralization). Security concerns around smart contracts aren’t just DeFi’s challenge—they’ll impact all on-chain projects, from GameFi to SocialFi. DeFi is paving the way, laying a foundation for safer protocols in the future.
3. Censorship Resistance
Censorship resistance is often overlooked, as many users focused on trading assume it’s irrelevant to them. However, experiencing a single instance of censorship—such as frozen funds or restricted access—reveals its importance. Censorship resistance ensures your assets remain truly yours, making it a cornerstone of the decentralized vision. In this regard, decentralized systems clearly outshine centralized ones, complementing asset sovereignty.
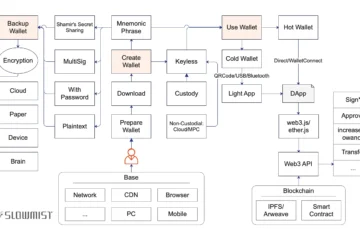
4. Wallet Security
On-chain asset storage typically involves cold wallets, hot wallets, or hardware wallets, each with distinct security profiles.
- Cold Wallets: These are created and managed entirely offline, often using devices like an old iPhone. Tutorials for setting up cold wallets are widely available online. Their security is high, provided you safeguard the physical record of your seed phrase.
- Hardware Wallets: Unlike cold wallets, hardware wallets rely on specialized devices with offline private key generation. However, the centralized nature of manufacturers introduces theoretical risks. Hardware wallets add an extra verification step, akin to a security token, before transactions.
- Hot Wallets: These are the most convenient for daily use, especially for frequent on-chain interactions like signing or authorizing contracts. However, authorizing upgradable contracts can introduce risks, as future updates may create vulnerabilities not present initially.
Wallet security ultimately hinges on protecting private keys and permissions. Users should tailor their wallet choices to their needs, balancing convenience with risk.
Conclusion
Crypto users must navigate a complex landscape of risks, from managing asset sovereignty to securing wallets and understanding smart contract vulnerabilities. By staying informed and adopting robust security practices, you can better protect your assets in this evolving ecosystem.