Navigating the Crypto Dark Forest: Your Essential Security Guide

As the crypto ecosystem evolves, the battle between security and malicious attacks intensifies. This guide will:
- Propose a taxonomy for classifying crypto security incidents;
- Highlight the most lucrative attack methods used by hackers;
- Review the pros and cons of current tools for preventing attacks;
- Discuss the future of crypto security.

1. Types of Crypto Attacks
The crypto application ecosystem consists of interoperable protocols powered by smart contracts, relying on blockchain and internet infrastructure. Each layer of this stack has unique vulnerabilities. We can classify crypto attacks based on the exploited layer and method.
Infrastructure Attacks
These target weaknesses in the underlying systems of crypto applications: blockchains for consensus, internet services for frontends, and tools for private key management.
Smart Contract Language Attacks
These exploit vulnerabilities in smart contract languages like Solidity, such as reentrancy or risky delegatecall functions, which can be mitigated by adhering to secure coding practices.
Protocol Logic Attacks
These leverage flaws in an application’s business logic. If a hacker finds a logic error, they can trigger unintended behavior. For example, a new decentralized exchange (DEX) with a flawed equation for calculating user payouts could allow hackers to extract more funds than intended. Protocol logic attacks can also target governance systems controlling application parameters.
Ecosystem Attacks
Many high-profile attacks exploit interactions between multiple applications. Typically, hackers use a logic flaw in one protocol, amplified by funds borrowed from another, often via flash loans. With flash loans, attackers borrow vast sums from protocols like Aave or dYdX without collateral, execute an attack, and repay the loan in a single transaction.
2. Data Analysis
Analyzing a dataset of the 100 largest crypto hacks since 2020, totaling $5 billion in stolen funds, reveals key trends:
- Ecosystem attacks are the most frequent, accounting for 41% of incidents.
- Protocol logic vulnerabilities cause the highest financial losses.
- The top three attacks were the Ronin Bridge ($624 million), Poly Network ($611 million), and BSC Bridge ($570 million).
- Excluding the top three, infrastructure attacks lead in total funds stolen.
3. How Do Hackers Strike?
Infrastructure
In 61% of infrastructure attacks, private keys are compromised through unknown means, often via social engineering like phishing emails or fake job ads.
Smart Contract Language
Reentrancy attacks are the most common at this level. In these, a vulnerable contract’s function calls a malicious contract, or a token transfer to a malicious contract triggers a function that recursively calls the vulnerable function before the contract updates its balance. For example, in the SirenProtocol hack, a function for withdrawing staked tokens was reentered repeatedly, draining all collateral.
Protocol Logic
Most protocol-level vulnerabilities are application-specific, as each app has unique logic (unless it’s a direct fork). Access control errors are the most common recurring issue. For instance, in the Poly Network hack, the “EthCrossChainManager” contract had a function anyone could call to execute cross-chain transactions. Forks of vulnerable codebases, like Compound’s, have also been hit. Projects like CREAM, Hundred Finance, and Voltage Finance suffered reentrancy attacks because they forked Compound’s code without vetting new tokens for vulnerabilities, unlike Compound’s rigorous process.
Ecosystem
Flash loans are used in 98% of ecosystem attacks. These typically follow a pattern: borrowing funds to manipulate token prices on an automated market maker (AMM) used as a price feed, then using inflated tokens as collateral to secure outsized loans.
4. Where Do Hackers Strike?
Analyzing the dataset by blockchain, Ethereum accounts for 45% of hacks, followed by Binance Smart Chain (BSC) at 20%. Reasons include:
- Ethereum and BSC have the highest total value locked (TVL), offering bigger rewards.
- Most developers use Solidity, supported by sophisticated tools, increasing activity on these chains.
Ethereum saw the most stolen funds ($2 billion), followed by BSC ($878 million). Cross-chain bridge or multi-chain app attacks, though only 10% of incidents, accounted for $2.52 billion in losses.
5. How to Prevent Hacks?
Each layer of the threat stack requires specific tools to detect and prevent attacks early.
Infrastructure
Most major infrastructure hacks involve stolen sensitive data like private keys. Robust operational security (OPSEC) and regular threat modeling reduce risks. Teams with strong OPSEC:
- Identify sensitive data (private keys, employee info, API keys);
- Assess threats (social engineering, technical exploits, insider risks);
- Identify gaps in existing defenses;
- Prioritize vulnerabilities by threat level;
- Implement mitigation plans.
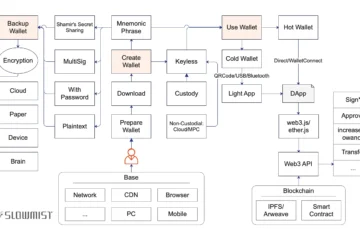
Using cold wallets (offline hardware or paper wallets) for private key storage minimizes hacking risks, as they never expose keys to the internet.
Smart Contract Language and Protocol Logic
- Fuzzing Tools
Tools like Echidna test smart contracts with random transactions to identify edge cases where unexpected results occur, ideal for catching logic flaws. - Static Analysis
Tools like Slither and Mythril automatically detect common vulnerabilities in smart contracts. They’re effective for known issues but miss problems outside their predefined scope. - Formal Verification
Tools like Certora compare smart contracts against developer-written specifications, ensuring the code behaves as intended (e.g., requiring sufficient collateral for loans). However, they’re only as good as the specifications; vague or lax specs miss errors. - Audits and Peer Reviews
Trusted developers review code during audits, producing reports on vulnerabilities and fixes. Third-party audits catch oversights but aren’t foolproof, as auditors are human and may miss issues or, in rare cases, exploit them.
Ecosystem Attacks
Few tools directly prevent ecosystem attacks, as automated tools focus on single-contract errors, and audits often miss multi-protocol interactions. Monitoring tools like Forta and Tenderly Alerts provide early warnings for composability attacks, but flash loan attacks often occur in a single transaction, rendering alerts too late. Threat detection models can flag malicious transactions in the mempool (before processing), but hackers can bypass this using services like Flashbots to send transactions directly to miners.
Forta uses AI-powered detection to integrate with protocols, offering real-time transaction prevention at the sequencer level, protecting apps like those on Celo. Pessimistic Spotter complements Forta by providing push notifications for suspicious contract deployments, factoring in parameters like fund sources and flash loans. Combining these tools has detected attacks on protocols like micDAO and Onyx Protocol seconds to minutes before public alerts.
6. The Future of Crypto Security
I predict two trends for crypto security’s future:
- Security as a Continuous Process
Top teams will shift from event-based security (testing → peer review → audit) to a continuous process, including:- Running static analysis and fuzzing on every code addition;
- Conducting formal verification for major upgrades;
- Building monitoring and alert systems with response actions (e.g., pausing apps or modules);
- Assigning team members to maintain security automation and attack response plans.
Security must persist beyond audits. For example, the Nomad Bridge hack stemmed from a vulnerability introduced in a post-audit upgrade.
- Organized Community Response
Crypto security communities will streamline hack responses. Currently, contributors flood group chats to help, but disorganization risks losing critical details. In the future, these efforts will become structured:- Using on-chain and social media monitoring for rapid attack detection;
- Leveraging security information and event management tools for coordinated workflows;
- Separating tasks (e.g., white-hat/black-hat efforts, data analysis, root cause analysis) into distinct channels.
By adopting these practices, the crypto ecosystem can evolve from a “dark forest” of lurking threats into a safer, more resilient space.