SlowMist: Risks in the Blockchain Dark Forest and How to Stay Safe
First, congratulations! You’re reading this guide. Whether you hold cryptocurrency, plan to, or are just curious, this handbook is worth studying and applying cautiously.
Second, brace yourself: this guide assumes some background knowledge. I’ll try to accommodate beginners, but it’s tough. Don’t fear the learning curve—much of this can be learned by experimenting. If you hit an unfamiliar concept, Google it. A key safety principle: cross-reference at least two sources for any online information, and always stay skeptical.
Yes, always stay skeptical—even of this guide’s advice! 🙂
Blockchain is a groundbreaking invention, revolutionizing trust by enabling tamper-proof, automated, and non-repudiable systems without centralized intermediaries. But reality is harsh. Misconceptions about blockchain create vulnerabilities, letting bad actors exploit wallets and cause massive losses. The blockchain world is a dark forest.
In this dark forest, live by two core safety laws:
-
Zero Trust: Always stay skeptical.
-
Continuous Verification: Verify anything you doubt, and make it a habit.
Note: All safety principles in this guide stem from these two laws.
Let’s dive into the dark forest with a visual guide to key activities—wallet creation, backup, and usage—and explore the risks and countermeasures.
A Visual Overview
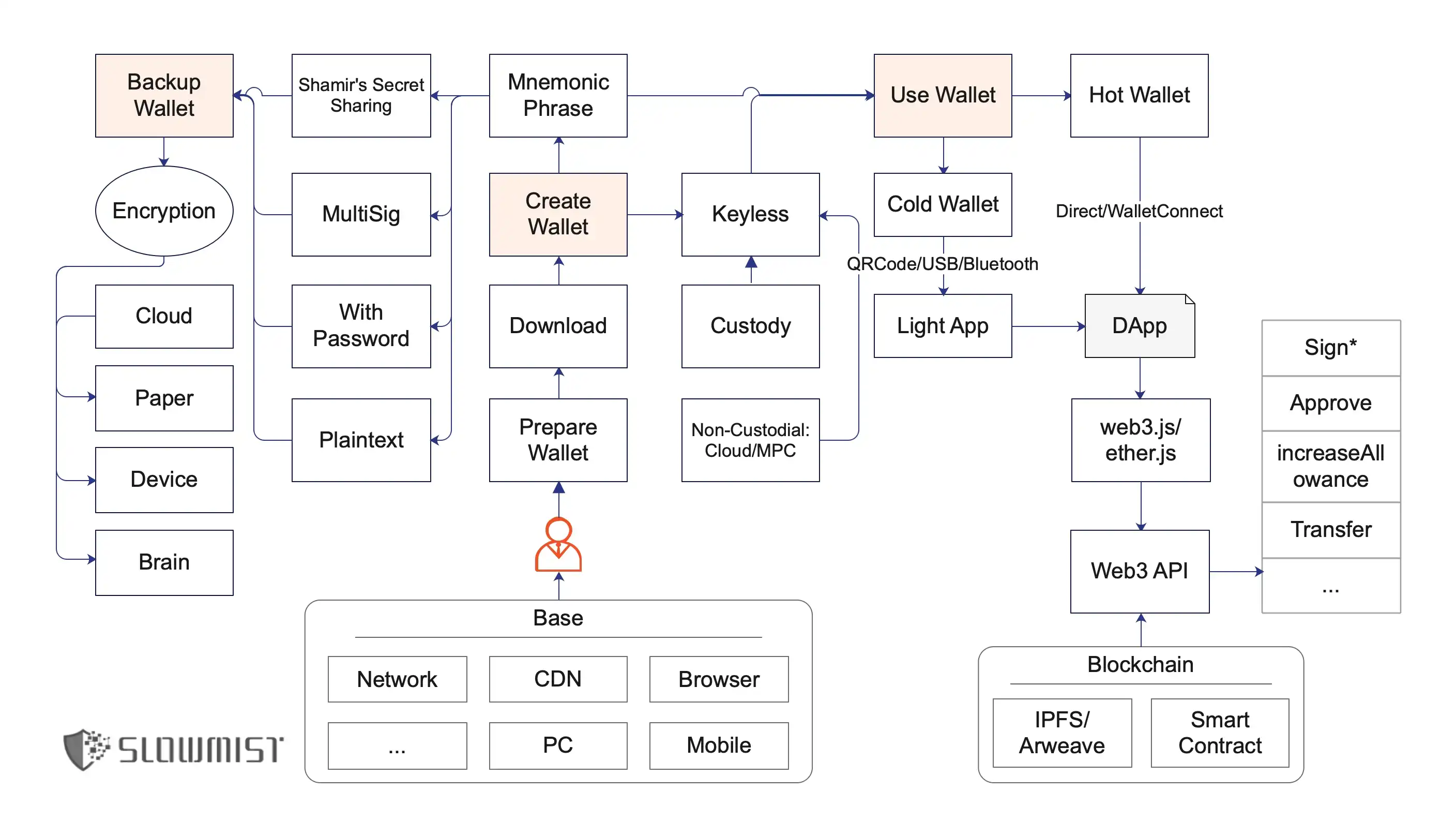
Before diving into details, glance at this diagram (imagine a flowchart of wallet-related activities). It outlines three core processes in the blockchain world (call it blockchain, crypto, or Web3): creating a wallet, backing it up, and using it. We’ll break down each process, analyzing risks at every step.
Creating a Wallet
The heart of a wallet is its private key or seed phrase (mnemonic).
A private key looks like this:
0xa164d4767469de4faf09793ceea07d5a2f5d3cef7f6a9658916c581829ff5584
A seed phrase looks like this:
cruel weekend spike point innocent dizzy alien use evoke shed adjust wrong
Note: This uses Ethereum as an example. Research private keys/seed phrases for deeper understanding.
Your private key is your identity. If it’s lost or stolen, your identity—and assets—are gone. Many wallet apps exist, and I’ll mention some trusted ones, but I can’t guarantee their safety or predict unforeseen risks. Always apply the two safety laws.
Wallets come in various forms: PC wallets, browser extensions, mobile apps, hardware wallets, and web wallets. They’re also classified as cold (offline) or hot (online). Your wallet choice depends on its purpose, which also shapes how you secure it.
One certainty: the longer you’re in this space, the more wallets you’ll have. This leads to a key safety principle: isolation. Don’t put all your eggs in one basket. Frequently used wallets are riskier. When exploring new projects, use a separate wallet with small funds until you’re confident. Even I, with years of experience, get wet shoes sometimes—nobody’s immune.
Downloading Wallets
Downloading a wallet seems simple, but it’s a minefield:
-
Many people (too many) download fake wallets from phishing sites or rogue app stores.
-
Most don’t verify if downloaded apps have been tampered with.
These mistakes can empty your wallet before you start.
To avoid fake downloads:
-
Google carefully, cross-referencing results.
-
Check trusted aggregators like CoinMarketCap.
-
Ask reliable contacts for recommendations.
Combine these sources to confirm the official website. Congratulations, you’ve found it!
Next, download and install. For PC wallets, follow the official link, but verify integrity before installing. This won’t catch insider tampering (e.g., a compromised developer or hacked site), but it prevents partial tampering or man-in-the-middle attacks. Common verification methods:
-
Hash Checks: Compare MD5 or SHA256 hashes. SHA256 is safer, avoiding MD5’s rare collision risk.
-
GPG Signatures: Use tools like GPG for robust verification. It’s tricky for beginners but worth learning.
Projects like Sparrow Wallet (a Bitcoin wallet) exemplify best practices, offering clear guides for both methods: Sparrow Wallet Download. Recommended GPG tools include GPG Suite (macOS) and Gpg4win (Windows), though their sites assume some prior knowledge.
For browser extensions like MetaMask, check Chrome Web Store metrics: MetaMask has over 10 million users and thousands of reviews, despite mixed ratings. Massive fake metrics are possible but unlikely to go unnoticed.
For mobile wallets, App Store regions matter. China’s App Store restricts crypto apps, so avoid using a Chinese account—switch to a U.S. account. Official sites for wallets like imToken or Trust Wallet guide you to legitimate downloads, but ensure the site itself is secure.
For hardware wallets (e.g., Ledger), buy directly from the official site, not marketplaces. Inspect packaging for tampering upon receipt. To be safe, create and record seed phrases three times, ensuring no duplicates in addresses or phrases, confirming randomness.
For web wallets, avoid them unless absolutely necessary. If forced, confirm the site’s legitimacy, use it quickly, and don’t get attached.
Seed Phrase Handling
Seed phrases, not private keys, are what you typically handle, as they’re human-readable. They follow standards like BIP39, usually 12 English words (or multiples of 3, up to 24). Fewer than 12 reduces security; over 24 is too complex. Hardware wallets like Ledger often use 24 words for extra caution. Words come from a fixed 2048-word list: BIP39 Wordlists. Non-English options (e.g., Chinese, Japanese) exist but follow the same standard.
When creating a wallet, seed phrase generation is sensitive. Ensure no one’s around, no cameras are active, and no spying devices are present. Verify the phrase’s randomness—trusted wallets use secure random number generators, but double-check. For cold wallets, create offline for maximum security. These habits, though tedious, become second nature and keep you safe.
Keyless Wallets
Keyless wallets eliminate direct private key handling, split into two types (my classification for clarity, not industry standard):
-
Custodial: Centralized platforms (e.g., exchanges) manage keys. You register an account, but security depends on the platform. Reputable platforms often compensate losses not caused by user error.
-
Non-Custodial: Users control a pseudo-key, not a direct crypto key. Examples include cloud-based authentication (relying on providers like Google) or Multi-Party Computation (MPC), which avoids single-point risks. Trusted MPC solutions like ZenGo, Fireblocks, and Safeheron combine security with smooth UX.
MPC benefits include mature algorithms, universal multi-signature (multisig) compatibility across blockchains, no single private key exposure, and cloud integration for usability. Drawbacks: limited open-source adoption and some argue Gnosis Safe suffices for Ethereum-based chains. Choose what feels secure and user-friendly.
Backing Up Your Wallet
Even experts, including me, have stumbled here. I once lost a wallet due to poor backup practices, saved only by SlowMist’s team cracking the issue. It wasn’t a major wallet, but it was a wake-up call. Let’s learn to back up securely.
Seed Phrase Types
Backing up a wallet means backing up its seed phrase (or private key, but I’ll focus on seed phrases). Seed phrases come in several forms:
-
Plaintext: The raw 12-24 words. You can obscure them with custom patterns (e.g., reordering, swapping words), but forgetting the pattern years later is a real risk. I learned this the hard way with a Ledger wallet, misordering 24 words and swapping some, only resolved by brute-force cracking.
-
Password-Protected: A password generates a unique seed from the same phrase, per BIP39. Back up both phrase and password. Private keys (e.g., via BIP38) or Ethereum’s Keystore files can also use passwords.
-
Multisig: Requires multiple signatures for transactions (e.g., 2-of-3 keys). Bitcoin wallets natively support multisig; Ethereum uses smart contracts like Gnosis Safe. MPC offers a universal multisig alternative.
-
Shamir’s Secret Sharing (SSS): Splits the seed into fragments (e.g., 20-word shards), requiring a threshold to restore. See best practices: Keystone SSS, Trezor SSS.
Multisig and SSS reduce single-point risks but increase complexity, often involving multiple parties. Balance convenience and security based on your needs.
Encryption
Encryption is vast—symmetric, asymmetric, or advanced. Good encryption ensures only you (or your disaster recovery delegate) can decrypt it years later, while others cannot.
Per the zero trust law, assume every backup step is vulnerable, even physical safes. Nobody, including yourself, is fully trustworthy—memory fades. But don’t paralyze yourself with fear; overcomplicating risks failure.
Disaster recovery is critical to avoid single-point risks. If you or your backup location are compromised, what’s the plan? Key strategies:
-
Trusted Delegates: Choose reliable disaster recovery contacts.
-
Multiple Backups: Store backups in diverse locations.
Backup locations include:
-
Cloud: Many fear cloud backups, but top providers like Google, Apple, and Microsoft invest heavily in security. Their internal controls and privacy protections are robust, though not infallible. Encrypt data before uploading. GPG is ideal for encryption and signing: GPG Tutorial. Back up GPG private keys and passwords securely.
-
Password Managers: Tools like 1Password (new versions support seed phrases) or Bitwarden offer convenience but slightly less security. I use them for less critical backups.
-
Paper: Hardware wallets often include durable paper cards for seed phrases. Steel plates (fire/water/corrosion-resistant) are an alternative. Verify the phrase after writing and store in a safe place, like a safe. Paper outlasts electronics if stored well.
-
Devices: Computers, iPads, iPhones, external drives, or USBs work, but electronics degrade. Use secure transfer methods like AirDrop or USB to avoid interception. Check annually for functionality. Encrypt as with cloud backups.
-
Memory: Memorizing phrases is thrilling but risky—memory fades, and accidents happen. Train your “memory palace,” but don’t rely solely on it.
Avoid over-encryption, which risks locking yourself out. Per the continuous verification law, regularly test backups, even partially, to ensure recoverability. Maintain confidentiality during verification.
Using Your Wallet
With your wallet created and backed up, the real challenges begin. If you’re passive, holding assets without interacting with DeFi, NFTs, or GameFi, your funds are relatively safe. But risks persist.
Anti-Money Laundering (AML) Risks
Even passive holders face risks—“trouble can strike from nowhere.” Where did your crypto come from? It didn’t appear magically. Your assets may trigger AML (Anti-Money Laundering) controls if linked to illicit activity. In extreme cases, assets like USDT can be frozen on-chain at Tether’s discretion, often at law enforcement’s request: USDT Banned Addresses. Check if an address is blacklisted via the USDT contract: Etherscan USDT.
Bitcoin and Ethereum aren’t frozen on-chain (yet), preserving decentralization. Most “crypto freezes” occur on centralized platforms like Binance or Coinbase, which block accounts, not chain assets. If your crypto is tied to a criminal case and enters a centralized platform, it risks freezing under AML rules.
Mitigate AML risks by transacting with reputable platforms or individuals. Advanced privacy tools like Tornado Cash exist but can be misused, so I won’t elaborate.
Cold Wallets
Cold wallets (offline) are inherently secure but require careful use. Receiving crypto is simple—use an observation wallet (e.g., imToken, Trust Wallet) to monitor addresses without exposing keys.
Sending crypto involves:
-
QR Codes
-
USB
-
Bluetooth
These pair with a networked Light App (e.g., observation wallets). The process:
-
Light App sends unsigned transaction data to the cold wallet.
-
Cold wallet signs with the private key and returns the signature.
-
Light App broadcasts the signed transaction.
QR codes have limited data capacity, requiring splitting for large transactions. These methods are secure but cumbersome. Risks include:
-
Address Verification Errors: Lazily checking only the first/last digits of an address can lead to transfers to a hacker’s spoofed address.
-
Unauthorized Approvals: Ethereum’s approve function can grant unlimited token access to malicious addresses if not vetted.
-
Deceptive Signatures: Some signatures hide traps (more later).
-
Insufficient UI Feedback: Cold wallets may not display enough transaction details, leading to errors.
These boil down to:
-
Lack of “what you see is what you sign” UX.
-
Insufficient user knowledge.
Hot Wallets
Hot wallets inherit cold wallet risks, plus the threat of seed phrase theft. Risks increase in compromised environments (e.g., malware-infected devices) or if the wallet has exploitable bugs.
Hot wallets interact with DApps (DeFi, NFTs, GameFi) via built-in browsers or WalletConnect to PC browsers. These interactions don’t typically expose seed phrases unless the wallet has design flaws. Historical audits show rare cases of malicious JavaScript stealing phrases, but top wallets like MetaMask avoid such errors.
My biggest concern isn’t these risks—they’re manageable. It’s wallet updates. How do we ensure new versions aren’t injected with malicious code or backdoors? Past incidents like CoPay and AToken involved:
-
Uploading seed phrases to hacker servers.
-
Swapping transaction addresses/amounts covertly.
-
Weakening random number generation for seed phrases.
For critical wallets, my principle is: don’t update unless necessary. If it works, stick with it.
DeFi Safety
DeFi safety (applicable to NFTs, GameFi) encompasses more than smart contracts, including:
-
Smart Contract Safety
-
Blockchain Foundation Safety
-
Frontend Safety
-
Communication Safety
-
Human Factor Safety
-
Financial Safety
-
Compliance Safety
Smart Contract Safety
Smart contract audits are critical: SlowMist Smart Contract Audit. Advanced users who can audit code or read audit reports may overlook other risks. A common issue is excessive permissions. Trusted projects like Compound mitigate this with Timelock mechanisms, delaying admin actions (e.g., 48 hours for Comptroller changes), giving users time to react. Multisig setups (e.g., Gnosis Safe) further reduce risks, but “fake multisig” (one party holding all keys) is a concern. Always verify multisig transparency.
Some projects deploy Timelocks with backdoors, creating false security. Audit reports help, but reading them takes practice.
Blockchain Foundation Safety
A blockchain’s consensus, virtual machine, and overall security are foundational. Choose reputable, battle-tested chains to minimize risks.
Frontend Safety
Frontend safety is a “devil” due to its proximity to users, often overlooked. Key question: How do I know the smart contract I’m interacting with is legitimate?
Risks include:
-
Insider Malice: Developers swapping contract addresses or injecting phishing scripts.
-
Third-Party Malice:
-
Supply Chain Attacks: Compromised third-party modules in frontend code.
-
Remote JavaScript: Malicious or hacked external scripts. HTML5’s Subresource Integrity (SRI) mitigates this by ensuring script integrity, but few projects (e.g., not OpenSea) use it: MDN SRI.
-
Communication Safety
Focus on HTTPS. Avoid HTTP sites, which are vulnerable to man-in-the-middle attacks. HTTPS certificate errors signal hijacking—stop immediately. The 2018 MyEtherWallet BGP hijacking incident saw hackers steal ETH via injected JavaScript after users ignored certificate warnings. Projects can enforce HSTS to block access on certificate errors, but many don’t.
Human Factor Safety
Insider malice (e.g., project team scams) is a human risk, covered earlier.
Financial Safety
Users prioritize stable prices and yields, expecting fair losses. Risks include unfair launches, whale manipulation, market crashes, or interdependent DeFi protocols exposing vulnerabilities. Technical attacks like front-running, sandwich attacks, and flash loans also threaten funds.
Compliance Safety
Compliance involves AML, KYC, sanctions, and securities risks. The 2022 AOPP controversy highlighted privacy concerns, with some wallets (e.g., Trezor) dropping support after backlash. Balance compliance with privacy based on your comfort.
DeFi safety is dynamic—audits are snapshots. Verify project updates against audit reports to catch discrepancies.
NFT Safety
DeFi safety principles apply to NFTs, but unique risks include:
-
Metadata Safety: Tampered metadata can misrepresent NFT assets.
-
Signature Safety: Malicious signatures can authorize theft.









